BTRFS Install (Kali Unkaputtbar)
Have you ever wished you could travel back in time after deleting that all important customer report or installing a broken driver just before heading into the board meeting?
Well, you better read on, because now you can!
All it takes is to install Kali Linux version 2022.1 or newer with btrfs as file system and to enable snapshotting after installation.
You can even boot into any of your saved snapshots via the boot menu and easily rollback to a previous system state:
Content
Content
Overview
Installation Overview
Partitioning Scheme
Kali Linux BTRFS Installation Steps
Kali Linux Installation Procedure
Usage
Modify configurations
Create additional configurations
Create a snapshot
List snapshots
Delete snapshots
Rollback
Diff
Browse snapshots
Full recovery from an unbootable system
Boot into a last known good snapshot
Rollback
References
Overview
btrfs is a modern Copy on Write (CoW) filesystem for Linux aimed at implementing advanced features such as pooling, snapshots, checksums, and integrated multi-device spanning. In particular, the snapshot support is what makes btrfs attractive for Kali installations on bare metal. Virtualization solutions such as VMware and VirtualBox provide their own snapshotting functionality and using btrfs in those environments is not really required.
The snapshotting strategy of this walk-through centres around a tool called “snapper” from our friends over at SUSE. Snapper transparently hooks into the apt workflow and automatically creates snapshots before and after any apt operation. This neat little feature allows to easily rollback a system after a botched upgrade.
To top things off, we added grub-btrfs by Antynea to automatically add a list of snapshots to the grub boot menu.
Snapper-gui by Ricardo Vieira is another great tool we use to make our lifes easier.
Installation Overview
Installing Kali Linux with snapshotting functionality is very similar to a standard installation except that we install it with btrfs as file system.
After the installation, we will install some tools and create a default configuration for snapper.
Partitioning Scheme
When selecting “btrfs” as file system, the installer will automatically create the following subvolume layout:
Kali Linux BTRFS Installation StepsKali Linux Installation Procedure
To start your installation, boot with your chosen installation medium. You should be greeted with the Kali Boot screen. Choose Graphical Install.
The installation steps are identical to a default Kali installation except changing “ext4” to “btrfs” as file system:
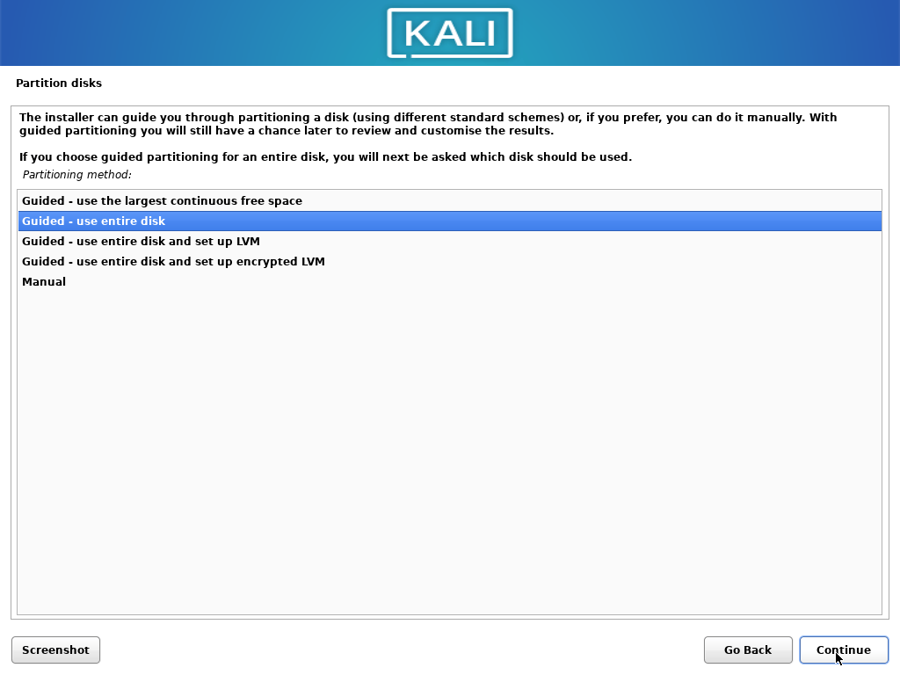
At the “Partition Disk” screen, choose “Guided - use entire disk”:
Click “Continue”:
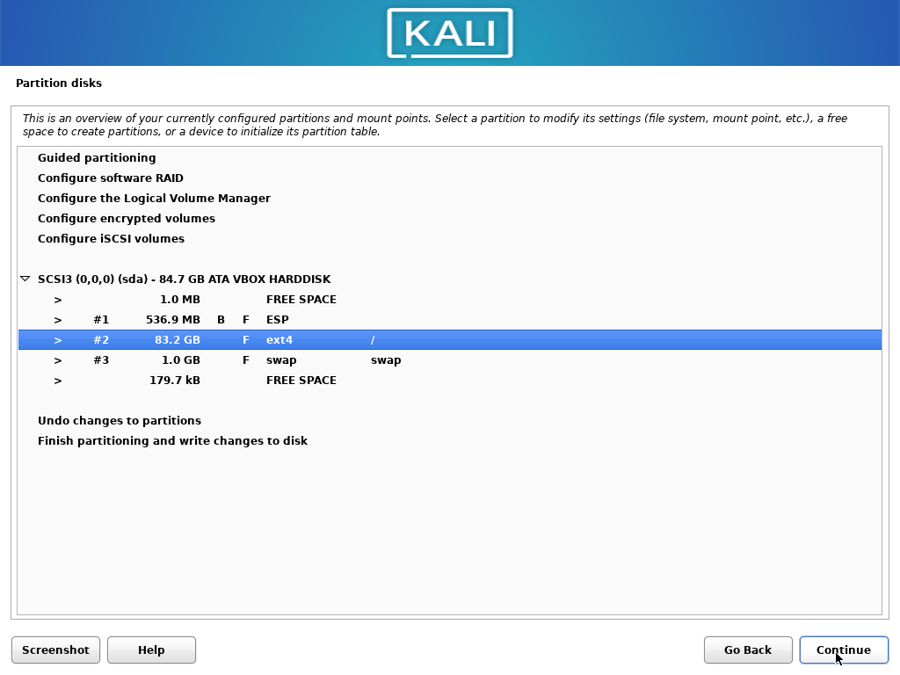
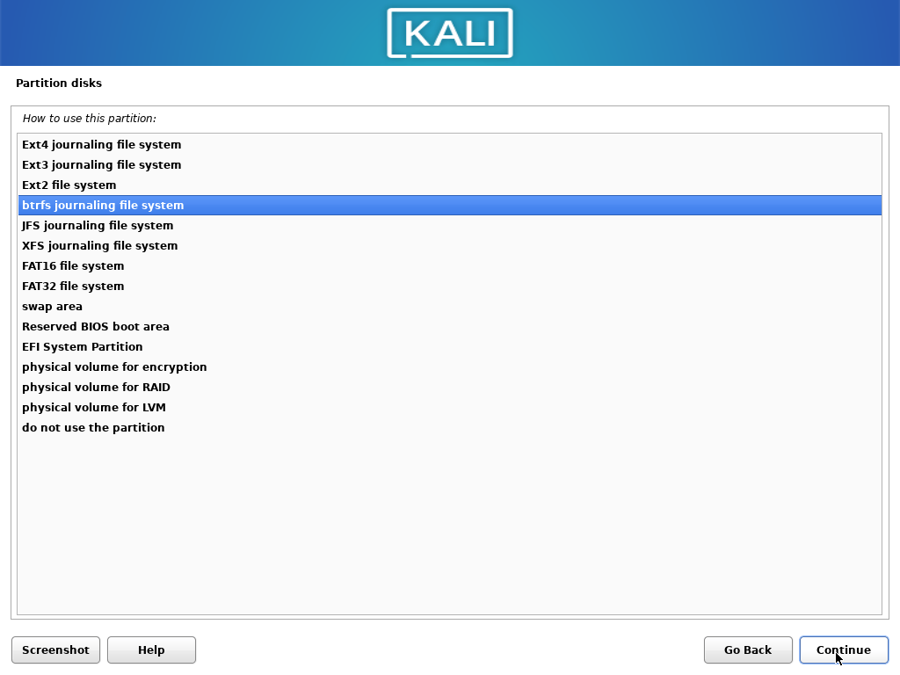
Double-click on the / partition:
Choose “btrfs”:
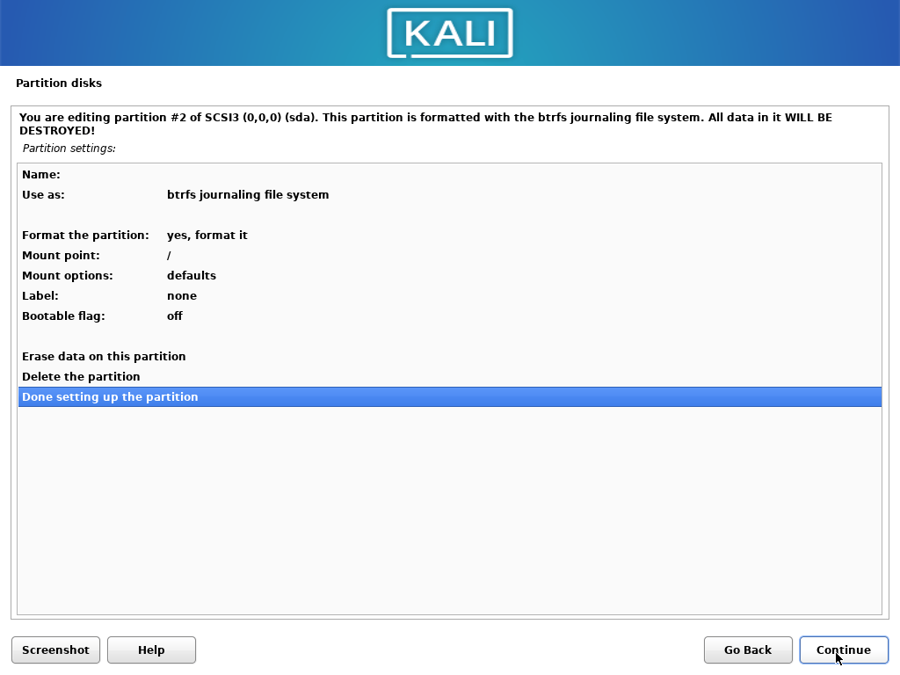
Select “Done setting up the partition” and continue:
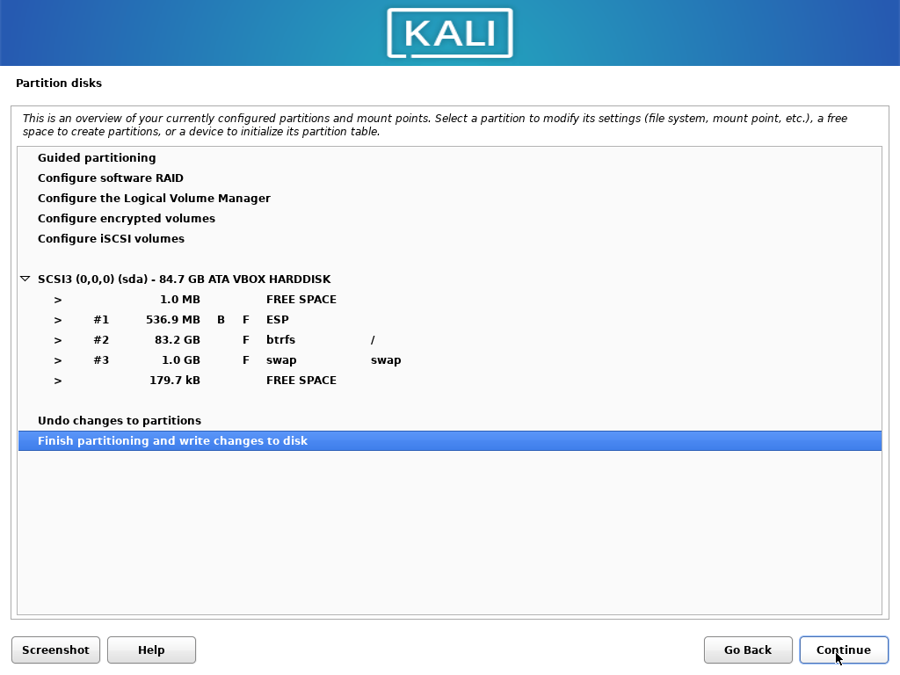
Select “Finish partitioning and write changes to disk” and continue with the installation.
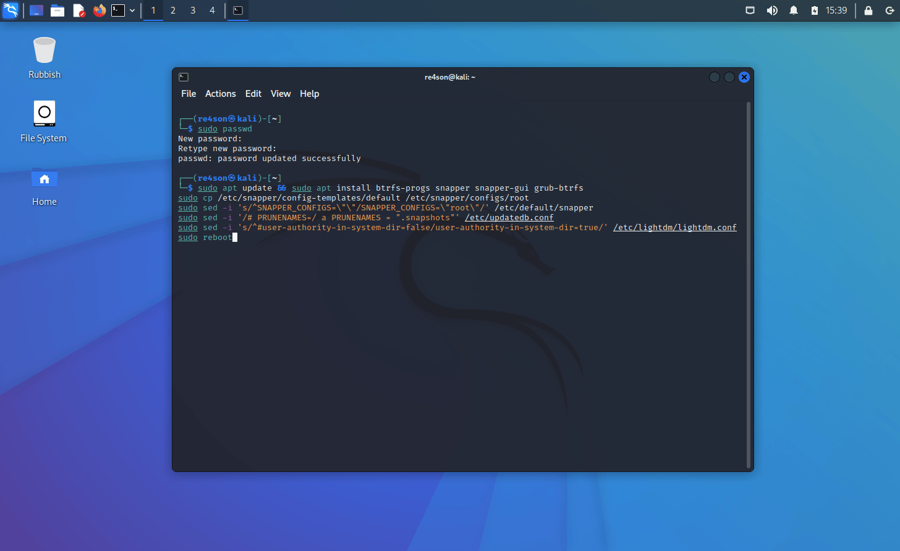
Login after installation and run the following commands in a terminal:
We need to tweak the desktop managers to work in read only snapshots. Pick your DE from the following:
GNOME:
KDE:
XFCE:
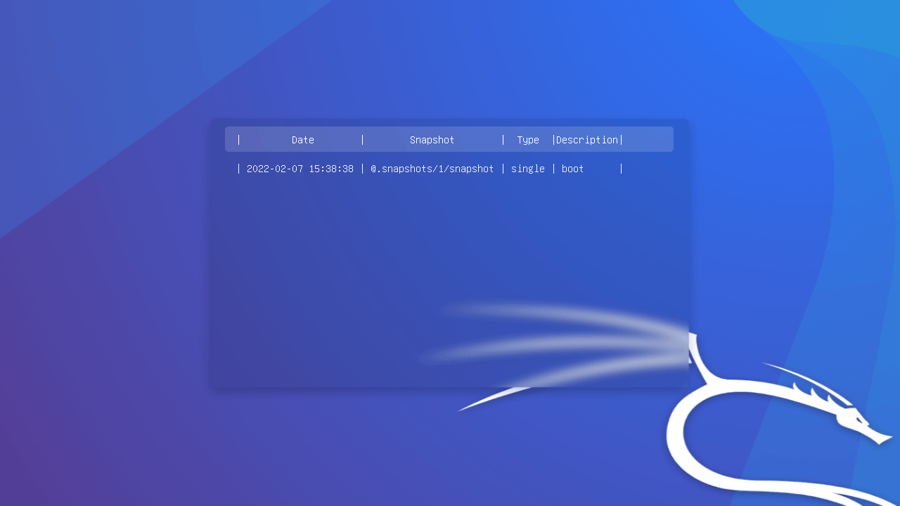
The first reboot will create the first automatic snapshot. Reboot again to find the new boot menu entry for this snapshot:
Congratulations, you have just installed a Kali system with automatic snapshotting functionality! Next, we will cover some basic usage examples.
UsageModify configurations
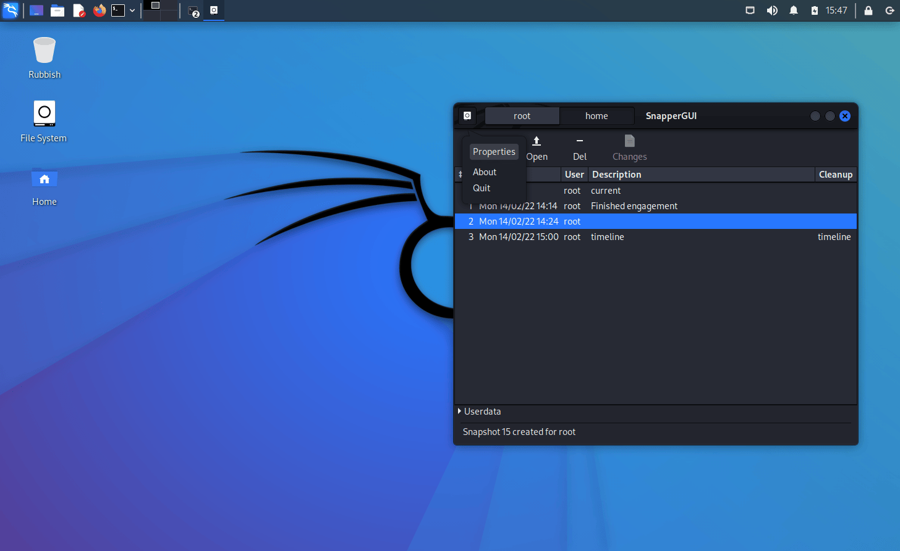
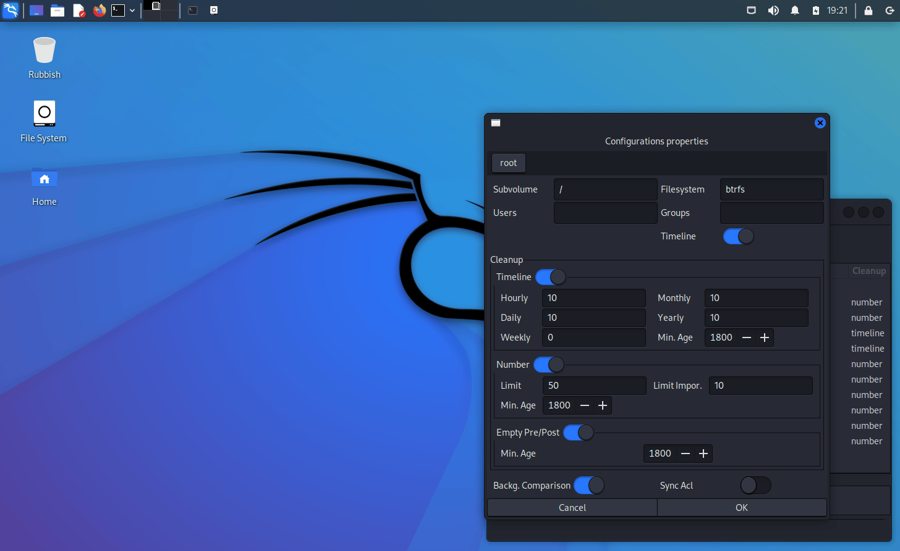
Out of the box Kali creates snapshots of the root directory to allow system rollbacks. Snapshots are automatically created during apt operations, at specified time intervals, and on every boot. The configuration can be changed via the “snapper-gui” tool. Just click on the little icon in the top left hand corner and select “Properties”:
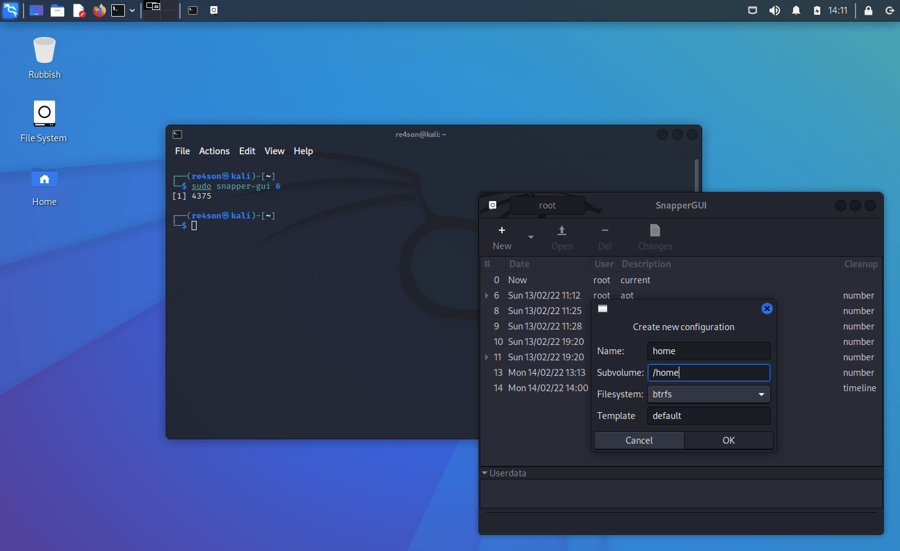
Create additional configurations
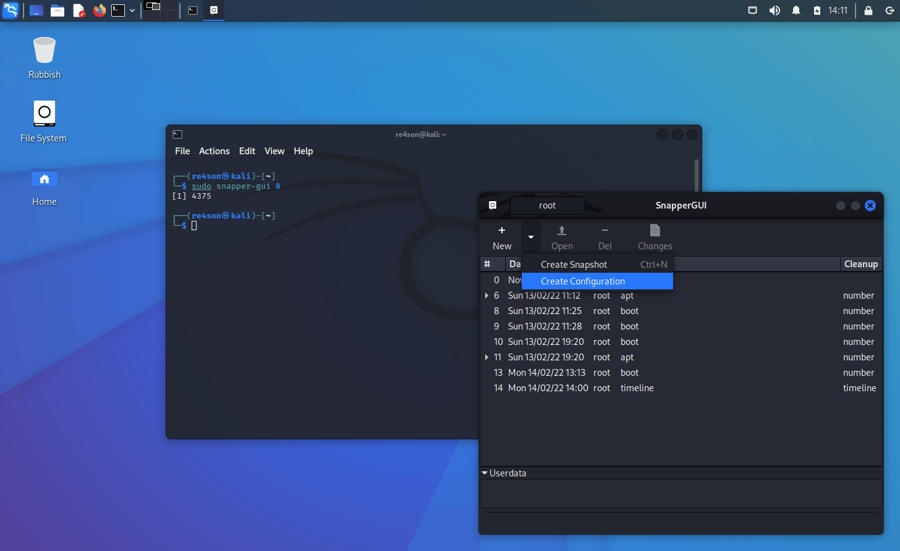
To create snapshots of your home directory, you can create a new configuration using snapper-gui.
Click on “New” -> “Create Configuration”
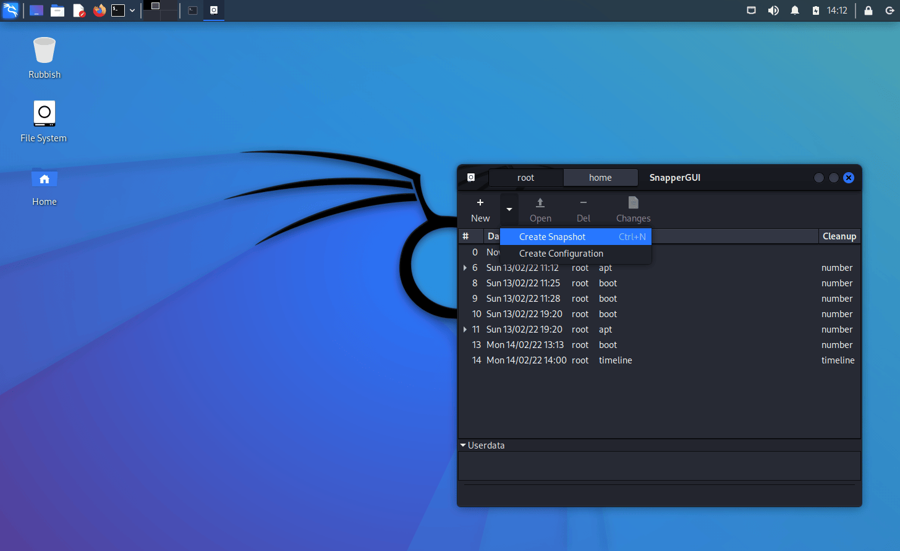
Create a snapshot
To manually create a snapshot using snapper-gui, select the appropriate configuration tab (home in this case) and click “New” -> “Create Snapshot”
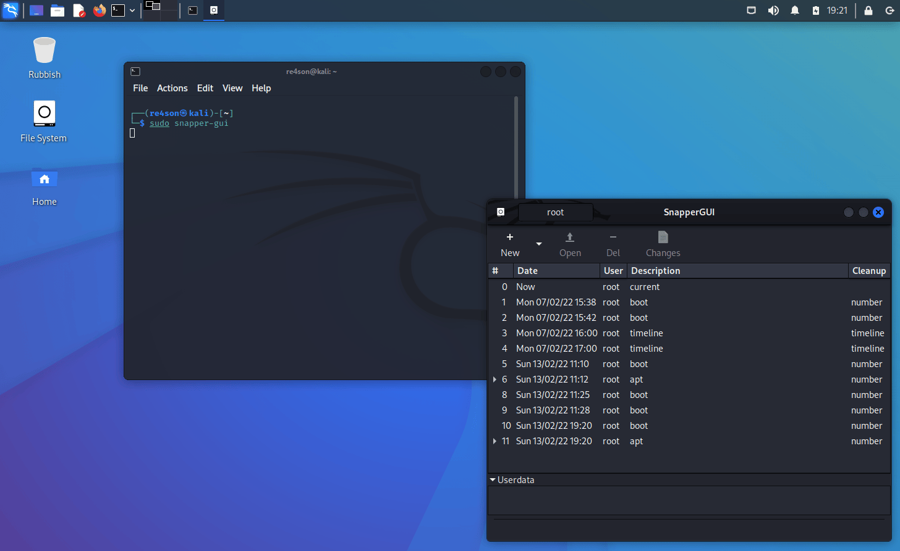
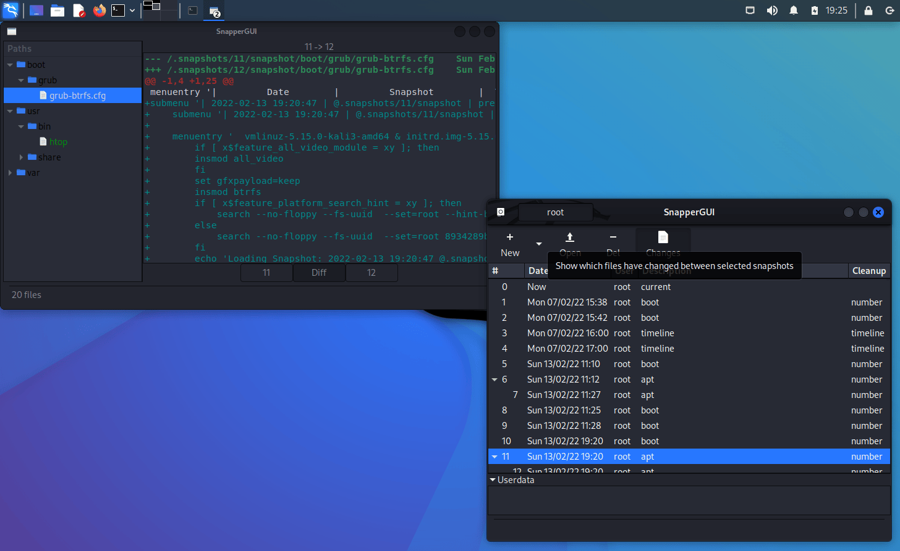
List snapshots
Snapshots are listed in the snapper-gui:
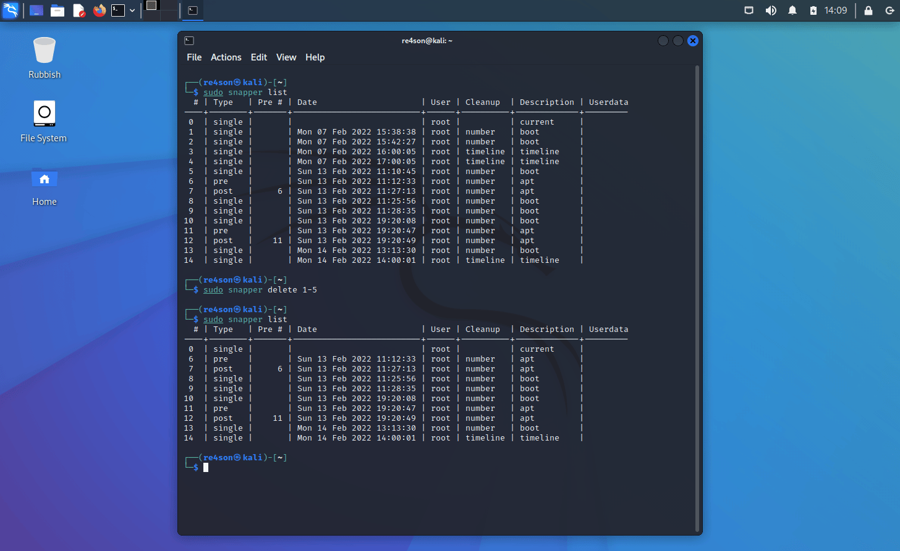
Alternatively, snapshots on all configurations can be viewed using the snapper command line tool:
Delete snapshots
The easiest way to delete a snapshot is by using the snapper command line tool:
sudo snapper delete <number-or-number-range>
Voilà, easy.
Now is probably the right time to flick through the snapper command line options via:
snapper --help
Rollback
To roll back to a previous snapshot we have to remember two things:
The root
/of the file system has been installed in a subvolume/@"and not the root of the btrfs partition/A snapshot is treated like just another subvolume except that they are read-only
You can easily boot into your read-only snapshots to find the one you want to roll-back to.
Thus all we have to do is mount the btrfs partition and replace the current root subvolume @ with the last snapshot. To be safe we’ll backup the current root (@) subvolume.
E.g.:
Diff
Snapper is chock-a-block with powerful features like diffs between snapshots:
Browse snapshots
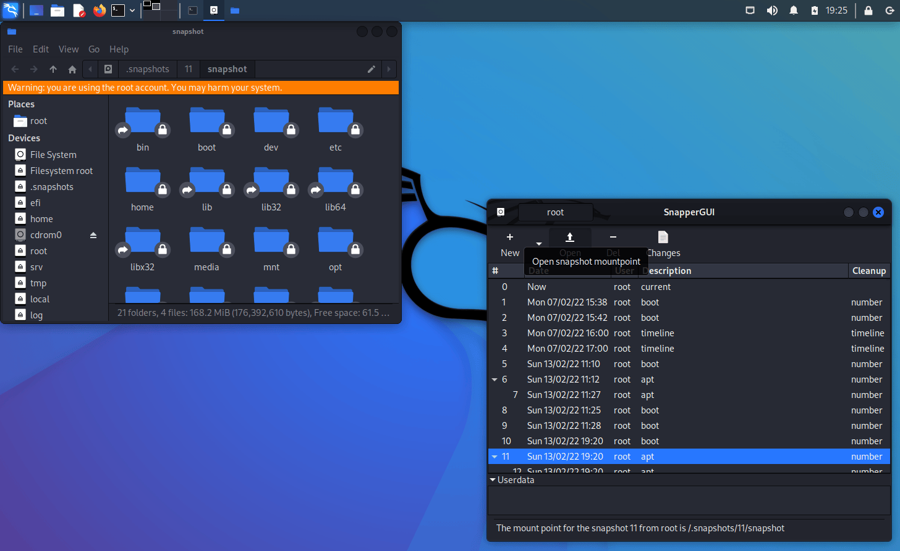
You can even browse the content of snapshots:
Full recovery from an unbootable systemBoot into a last known good snapshot
Let’s assume that the last upgrade broke our machine. Every run of “apt install” creates to snapshots, one “pre” snapshot is created before the installation and one “post” snapshot is created after the installation.
To undo the last “apt upgrade”, we would boot into the last “pre” snapshot and check if everything is working again:
Now you can login to the snapshot.
Please note that the snapshot is read only and you might receive an error message from an applet or two after logging in. Just ignore that.
Have a look around ensure that this is what you would like to roll-back to.
Rollback
Remember that “/” itself is the subvolume “@”. To rollback to a snapshot, all we have to do is replace “@” with the snapshot we want.
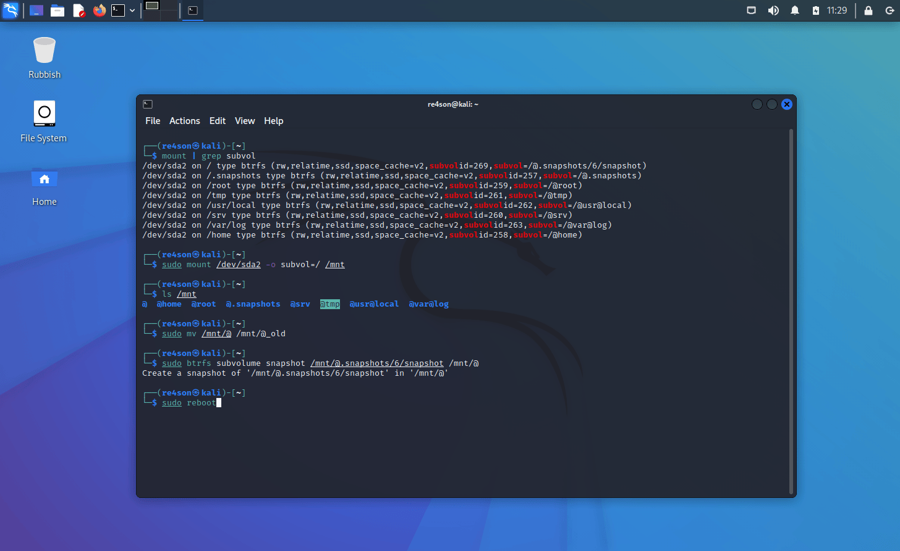
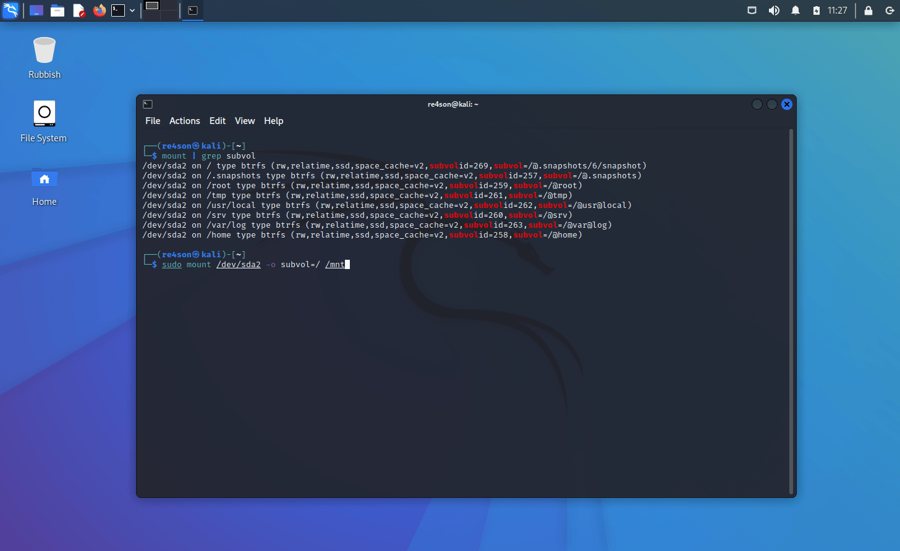
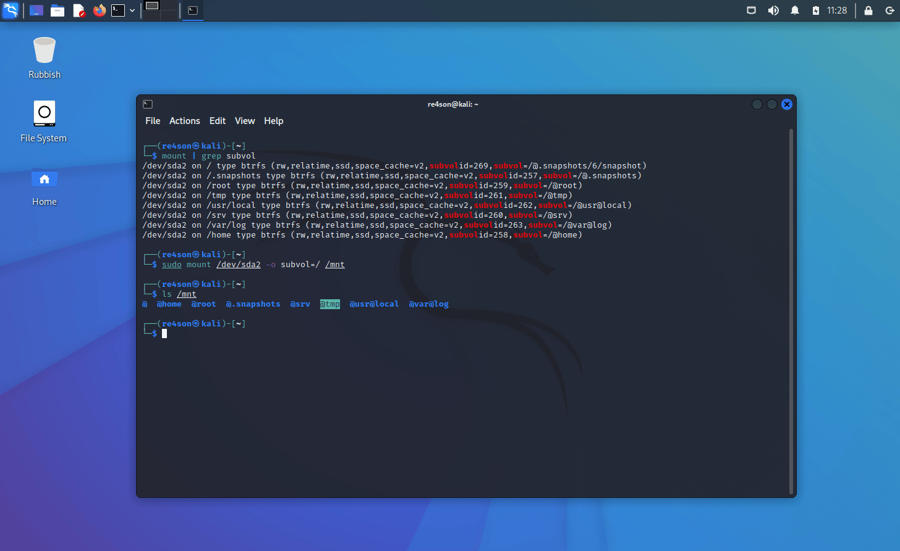
First we have to mount the physical partition that holds all our subvolumes. Let’s find it first
mount | grep 'subvol='
and then mount it (/dev/sda2 in this example:
sudo mount /dev/sda2 -o subvol=/ /mnt
If we list the content of that partition we can see all the subvolumes, including the one containing our snapshots:
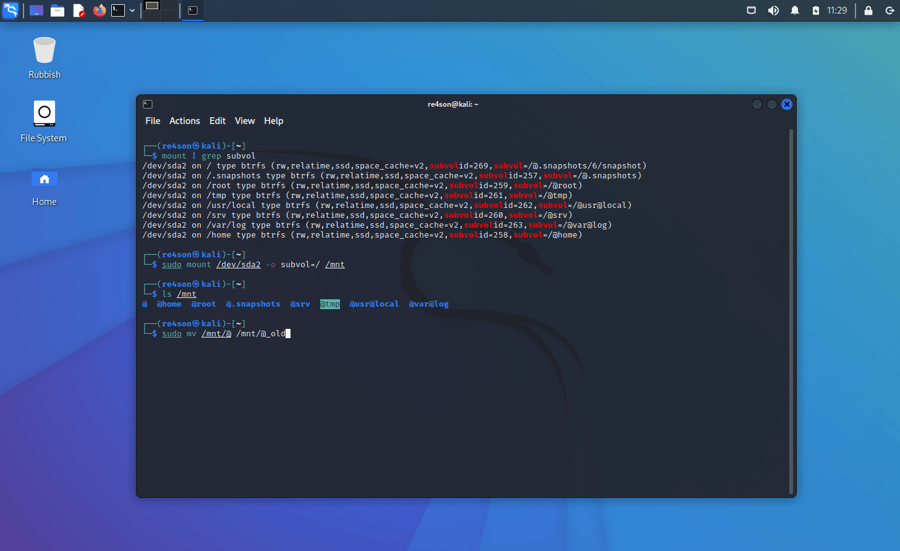
Before we replace the current root with our snapshot, let’s move “@” away just to be safe:
sudo mv /mnt/@ /mnt/@_old
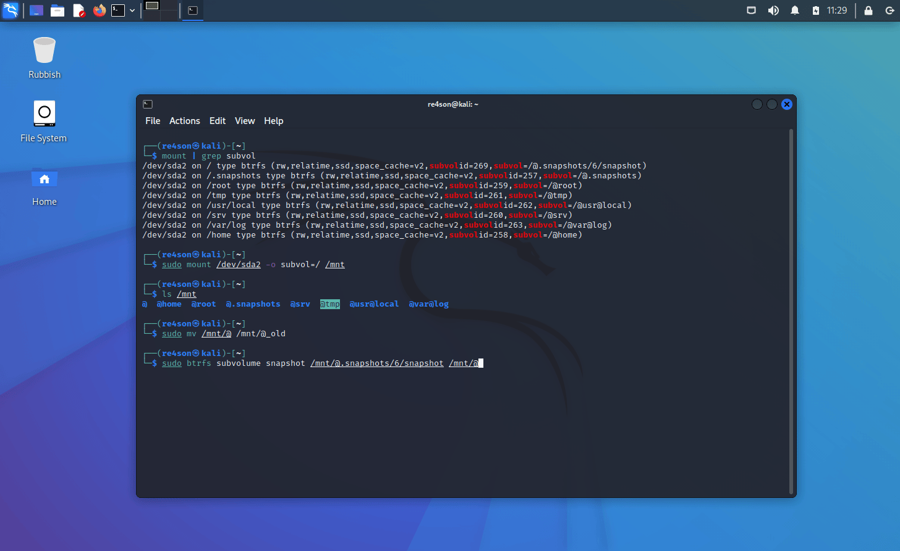
Now we can create a read-write snapshot of the current read-only snapshot (in this example we booted into the read-only snapshot “6” according to the query above):
sudo btrfs subvolume snapshot /mnt/@.snapshots/6/snapshot /mnt/@
And that’s all there is to it, now we can reboot as if nothing ever happened to our beautiful machine:
References
Last updated